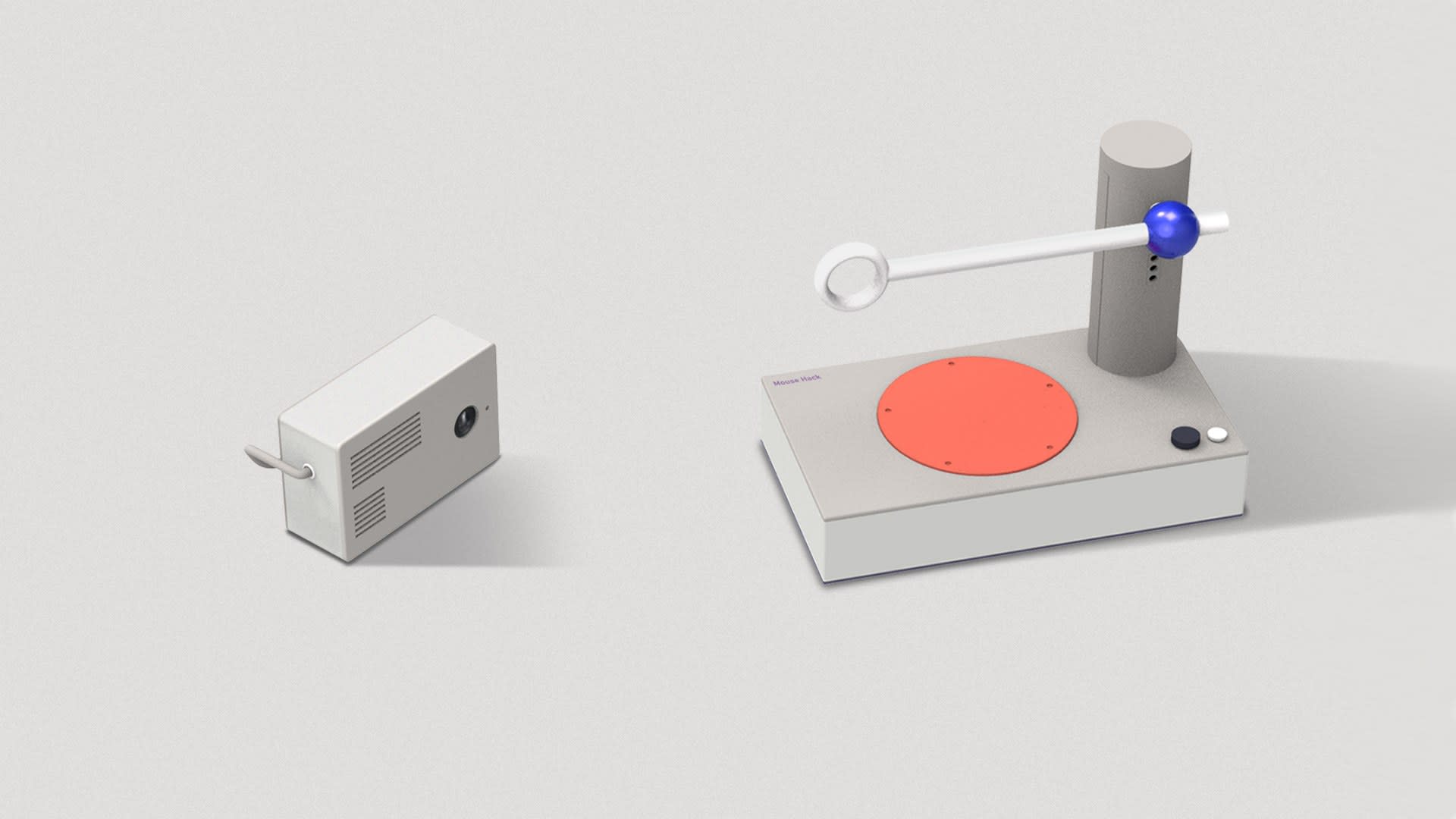
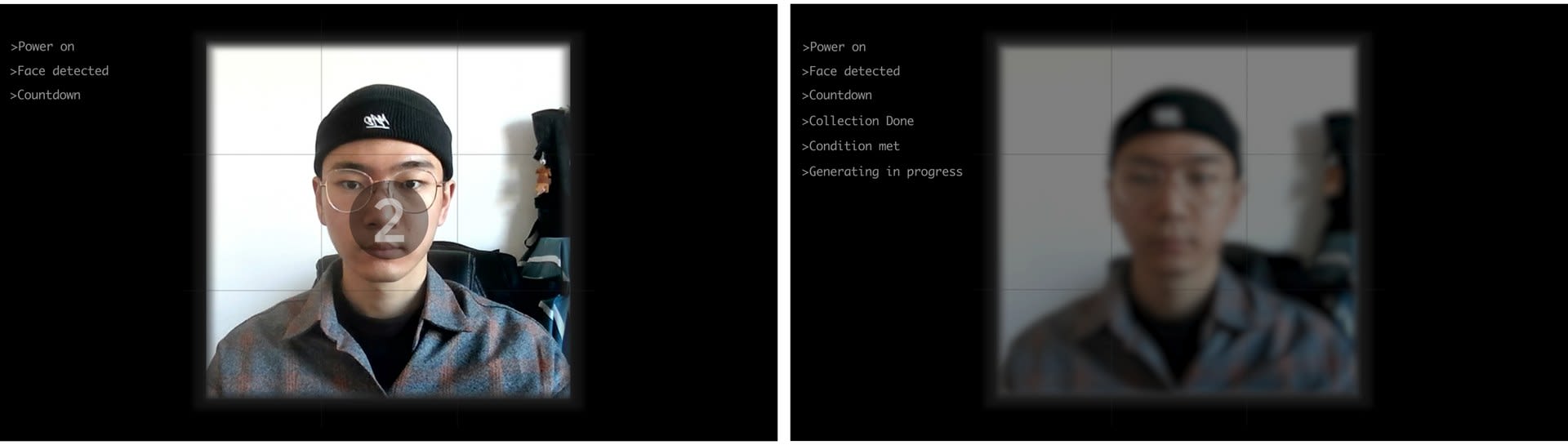
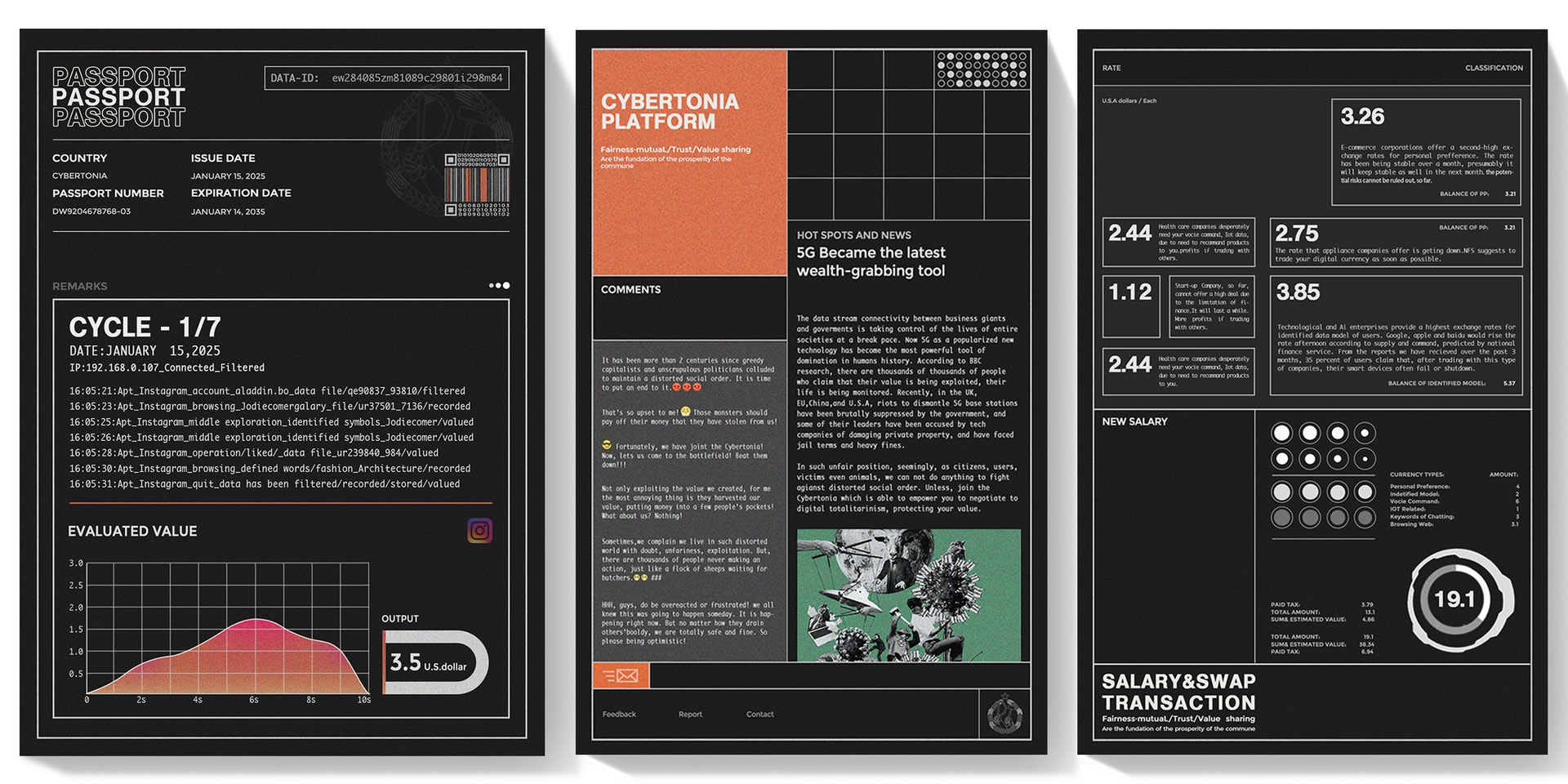
Boyu is an experienced industrial designer with an interdisciplinary background in the study. During the course of Design Future Platform at the RCA, he studied future design methodology with Professor. Carolina and Professor. Oron.Catts. As a senior design student, his curiosity spans different areas of interest from historical events, political & social movements, to emerging technologies. Exploring these areas with hidden connections has empowered him with a shifted perspective and unusual inspiration to envision future social trends.
He insists on basing design practice on solid historical research and current clues and optimizing its viability through multiple technology-driven iterations of prototype testing throughout his design journey.